Security Roles and Identities
Security Roles are used in conjunction with Security Identities to define much of the user access to entities within Keyfactor Command. From the Securities Roles and Identities page you can view the lists of security roles and security identities and manage your security configuration. For more information on security considerations in Keyfactor Command see Keyfactor Command Security Design Considerations.
Security Roles
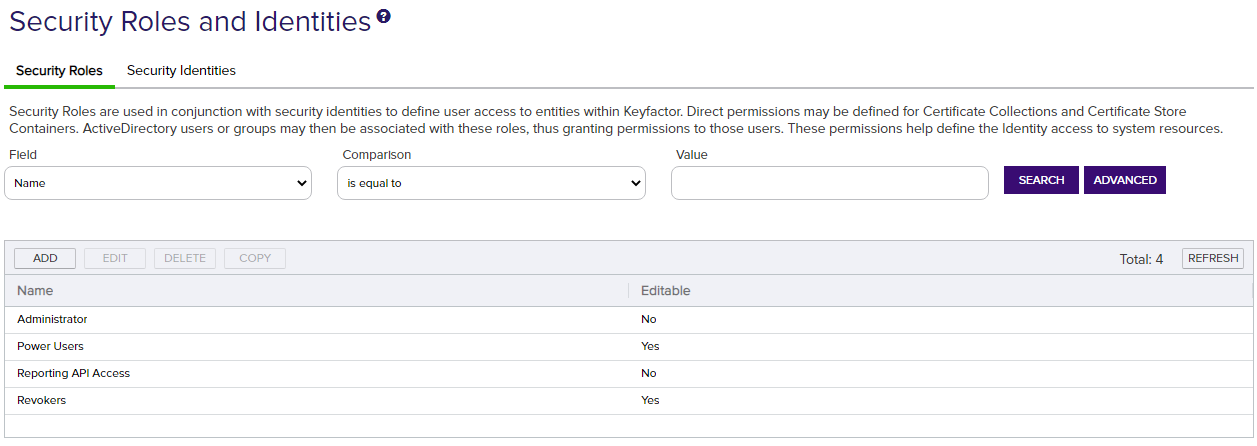
Figure 346: Security Roles
During the Keyfactor Command installation and configuration process, the security role Administrators is created (see Administration Section in the Keyfactor Command Server Installation Guide). The Administrators role grants full permissions to the Management Portal and cannot be edited or deleted. If all users of the Management Portal should have full access to all features within the portal, this one role will be sufficient for your needs. However, if you would like to grant access to other users but limit the functionality available to those users, you need to add one or more new security roles for this purpose.
A Reporting API Access role is automatically created during installation to support the dashboard and reporting access required by the Logi Analytics Platform. The service account used for the IIS application pool on the Keyfactor Command Management Portal server (where Logi is installed) is automatically created as an identity and associated with this role if you've opted to use integrated Windows authentication. If you've opted to use basic authentication, the user you enter on the Dashboard and Reporting tab of the configuration wizard in the Keyfactor API User field will be created as an identity and associated with this role.
Configuring security roles within Keyfactor Command (see Security Role Operations) has several effects. These roles are used to:
- Grant access to the Management Portal, by selecting menu access permissions for a role. See Security Role Permissions.
- Grant certificate collections access by selecting role permissions per collection
 The certificate search function allows you to query the Keyfactor Command database for certificates from any available source based on any criteria of the certificates and save the results as a collection that will be availble in other places in the Management Portal (e.g. expiration alerts and certain reports).. See Certificate Permissions.
The certificate search function allows you to query the Keyfactor Command database for certificates from any available source based on any criteria of the certificates and save the results as a collection that will be availble in other places in the Management Portal (e.g. expiration alerts and certain reports).. See Certificate Permissions. - Grant certificate store containers access by selecting role permissions per container. You can set and view the role container permissions from the Container Permissions page. See Container Permissions.
Security roles affect the Management Portal and the APIs only.
Security roles for SSH![]() The SSH (secure shell) protocol provides for secure connections between computers. It provides several options for authentication, including public key, and protects the communications with strong encryption. key management are structured somewhat differently than those for most of the rest of the product set, as they don't use the standard Read and Modify convention. For more information, see SSH Permissions.
The SSH (secure shell) protocol provides for secure connections between computers. It provides several options for authentication, including public key, and protects the communications with strong encryption. key management are structured somewhat differently than those for most of the rest of the product set, as they don't use the standard Read and Modify convention. For more information, see SSH Permissions.
Security Identities
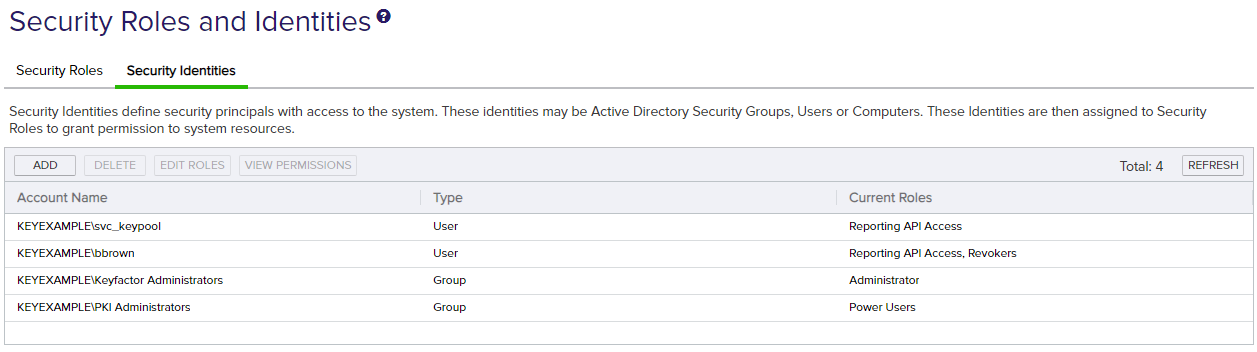
Figure 347: Security Identities
Identities are created in Keyfactor Command using Active Directory users or groups. During the Keyfactor Command installation and configuration process, administrative security identities are created using the Active Directory user or group record you entered on the Keyfactor Portal tab of the configuration wizard in the Administrative Users field (see Administration Section in the Keyfactor Command Server Installation Guide). More than one user or group may be entered during configuration, if desired. Identities entered in the configuration wizard are associated with the Administrators role that grants all permissions to the Management Portal.
If you would like to grant access to other users but limit the functionality available to those users, you need to add one or more new security identities for this purpose and link them to one or more appropriate security roles. See Security Identity Operations.
You can also find the help icon at the top of the page next to the Log Out button. From here you can choose to open either the Keyfactor Command Documentation Suite at the home page or the Keyfactor API Endpoint Utility.